Foundation for Google Chronicle
Ingest all your data at scale and speed. Observe everything across multiple tenants. Blazing fast setup takes a day.
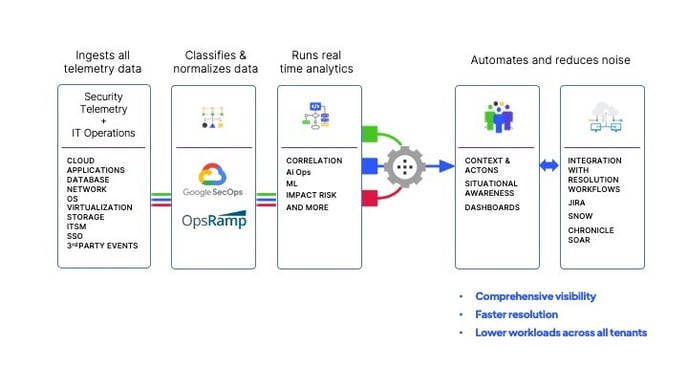
Resolution Intelligence Cloud is a cloud-native data analytics platform for managing risk and optimizing overall operations, with the scale and speed of Google Chronicle built in. Taking a cybersecurity mesh architecture (CSMA) approach, the platform ingests all data across security and digital operations, correlates alerts, identifies incidents and pre-incident situations, prioritizes them based on business risk, and provides extensive context for fast, proactive resolution. With the platform, you can:
“The important thing to remember about a platform like this is that all this data generation and analysis is done behind the scenes, by the automated systems built into the platform. By doing data analysis and correlation, the platform lets analysts and operators focus on solving problems and the tasks at hand.”
Ingest all your data at scale and speed. Observe everything across multiple tenants. Blazing fast setup takes a day.
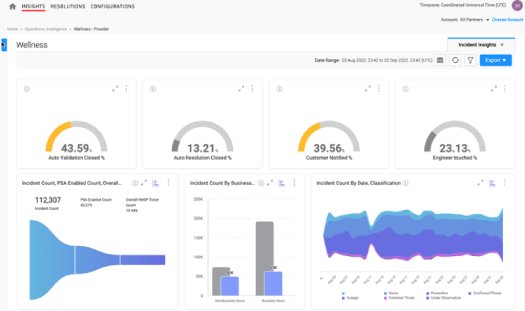
Discover what matters most. Gain situational awareness with real-time data analytics and machine learning that reveal anomalies, risky behaviors, and pre-incident situations
Resolve what matters, fast and proactively, with the right context and ActOns. Collaborate on resolution or use existing workflow.
Stop the barrage of alerts. ActOns correlate alerts with asset and user data so you can act decisively on what matters most to the business now.
Save time and sanity: stop chasing false positives and know where to focus with priority scores aligned to business risk.
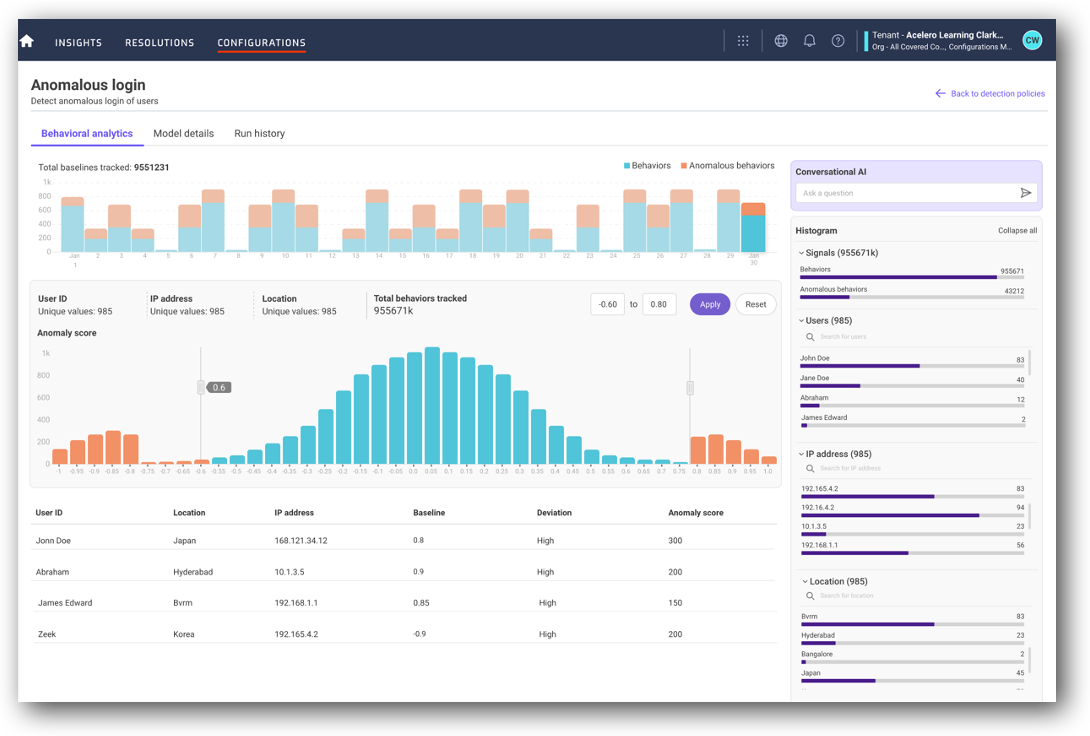
Detect unknowns with advanced anomaly detection, analytics, and ML across real-time data from hybrid cloud environments.
Create secure war rooms to collaborate with colleagues, customers, and other key stakeholders in a single place with extensive context.
Discover top vulnerabilities and map threat trends with Threat Hunting Services, vulnerability disclosures, and advisories.
Automate investigation and remediation tasks while providing your SOAR and ITSM with enriched context for faster resolution.
Resolution Intelligence Cloud ingests all your security and digital ops data, then identifies what matters most so you can proactively manage material risks to the business without constant fire drills.
Read about data ingestion and integrations.

It takes less than a day to set up the platform, multiple Resolution Intelligence Cloud tenants, and diverse data sources. Ingest terabytes in days.
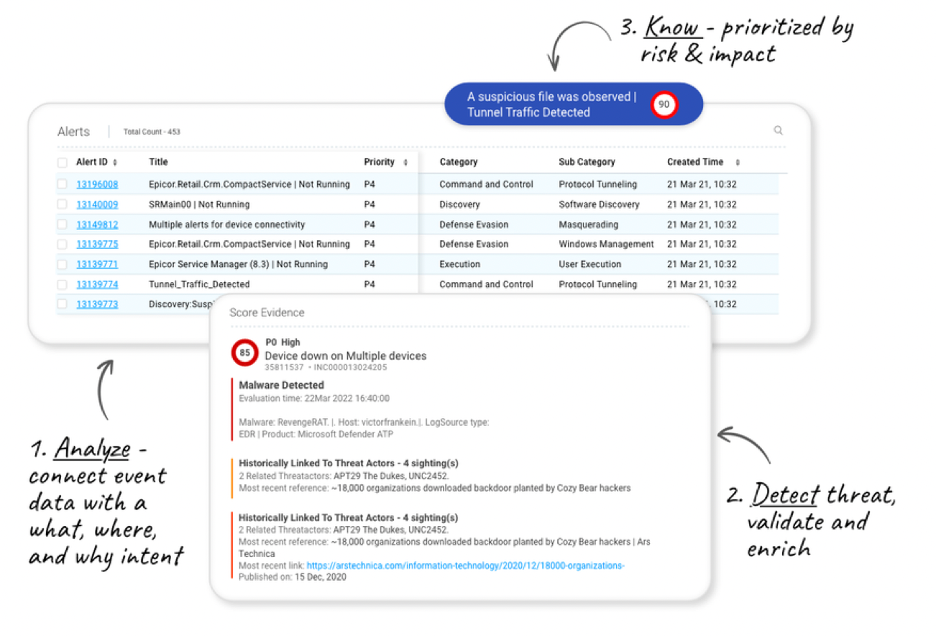
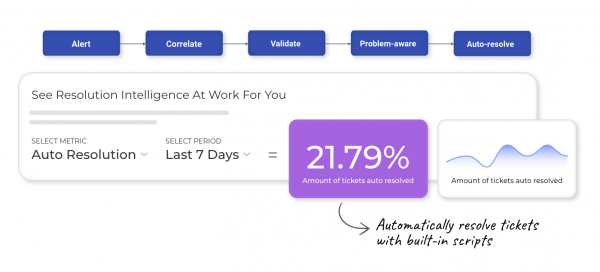
Boost efficiency and effectiveness with the information you need at your fingertips. Resolution Intelligence Cloud generates actionable insights you can act on, called ActOns. ActOns present highly curated, contextual data — like related alerts, asset, and user data. You can focus on what matters most because ActOns are prioritized based on a risk score that’s aligned to your business and derived from likelihood, impact, and confidence. Click on ActOns to dive into details and investigate further.
Start broader, dive deeper, and correlate relevant data with graph tools and a machine-learning (ML) toolkit.
Work from a complete picture with data across security and ops. Get insights at any level through dashboards that show what matters most.
Automate responses that don’t require humans in the loop. Reduce noise and enable staff to focus on tasks that require their expertise. Resolution Intelligence Cloud gives teams the context they need to take informed action.
Enjoy blazing fast, sub-second search on petabytes of data that's stored hot for a year. With one click, pivot to investigate incidents further. You maintain control of your Resolution Intelligence Cloud instances and IP.

Tenant-by-tenant management is time consuming and doesn’t scale. Resolution Intelligence Cloud adds multi-level multitenancy to your Google Chronicle instances. Log into Resolution Intelligence Cloud once to streamline rule- and parser-building, threat analytics, and event tracking across your entire base. Apply detection rules to all, some, or one tenant.
Identify and remedy detection gaps with automated log mapping to the MITRE ATT&CK framework. ActOns display a MITRE mapping of the correlated events detected, giving you instant insights.
.png?width=1000&height=469&name=detection-coverage-against-threat-actors-1024x480%20(1).png)








