Wise are the words Knowledge is a virtue and ignorance is vice in the cybersecurity industry. Netenrich’s threat intel platform and news aggregator, KNOW or Knowledge NOW delivers on this by providing actionable insights for cybersecurity professionals across the globe.
Free Knowledge NOW
Let’s take a look at the recap from March.
Black KingDom – Trending Malware in March
Black KingDom, somewhat amateurish and rudimentary in composition, still has a potential to cause a great deal of damage. This virus continues to wreck havoc by spreading through exchange servers that are not patched against the ProxyLogon exploit designated as CVE-2021-26855. This script executes the Win32_Process via WMI. As reported by researchers, this script can also infect other computers on the network.
Black KingDom Trends from KNOW
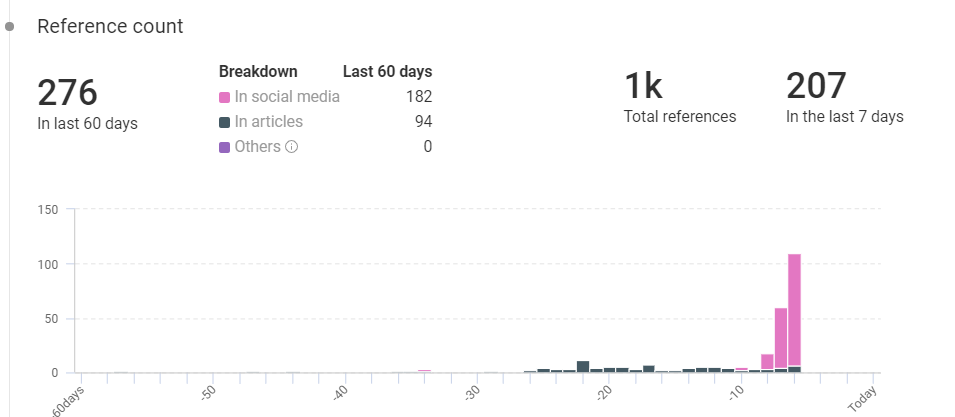
- Total references: 1000
- Last 60 days: 276
- Previous 7 days: 207
Twitter Reactions to Black KingDom
https://t.co/NZPRoV7Sy4 'Black Kingdom' Ransomware Hits Unpatched Exchange Servers #cybersecurity
— Security News (@netsecu) March 24, 2021
Black Kingdom ransomware is targeting Microsoft Exchange servers – https://t.co/uXKELruzkG #cybersecurity #cloud #network #news #hacking #darkweb #uk #us #israel #security #cybersec
— CyberSecurity News Feed (@GetinfosecN) March 24, 2021
Black Kingdom ransomware is targeting Microsoft Exchange servers https://t.co/ndNFnqY6GL pic.twitter.com/3dPlYz8uJ0
— EdiAcoo (@AcooEdi) March 24, 2021
Sodinokibi – Trending Malware in March
Also known as ‘REvil’, Sodinokibi is a (RaaS) Ransom-as-a-Service model which was discovered back in April 2019. This ransomware has multiple infection vectors with the ability to exploit known security vulnerabilities and carry out phishing campaigns. By using the vulnerability in Oracle WebLogic CVE-2019-2725, Sodinokibi can encrypt user files and gain administrative access.
It was in May 2019 that Sodinokibi grabbed attention when it exploited a Zero-Day flaw in Oracle and encrypted files on the targeted system. Once encrypted, hackers demanded a ransom of $2,500 which would then double to $5000 if the initial deadline was missed.
Why is Sodinokibi Trending?
Acer, a multinational hardware and electronics corporation based out of Taiwan was attacked by Sodinokibi ransomware. The attackers were successful in accessing the bank balances, bank communications, and financial spreadsheets as it compromised its Microsoft exchange Server Vulnerability.
KNOW Trending Ransomware
The ransomware gang has announced the hack on their data lead site, saying and asked for a massive $50 million ransom. This is the largest known ransom in history. Regarding the story, Acer said:
“Companies like us are constantly under attack, and we have reported recent abnormal situations observed to the relevant law enforcement and data protection authorities in multiple countries.”
Sodinokibi Trends from KNOW
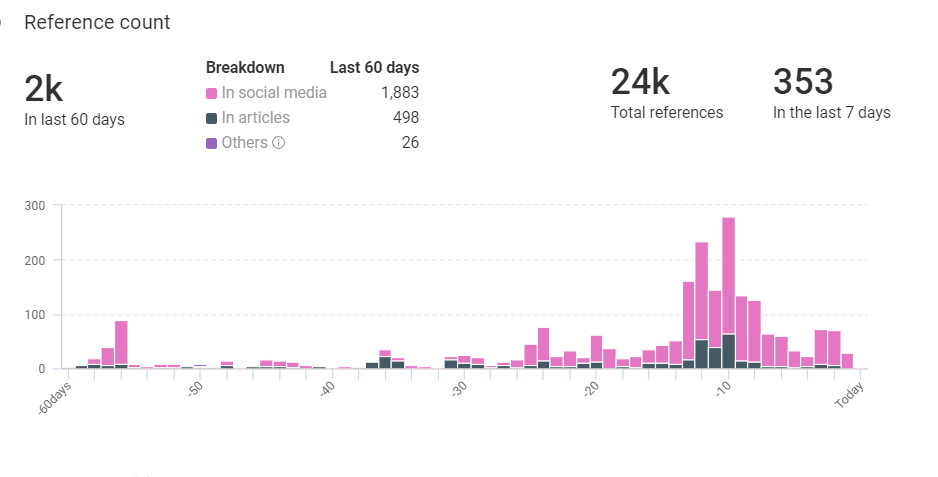
- Total references: 24,000
- Last 60 days: 2,000
- Previous 7 days: 1,000
Sodinokibi Context From KNOW
- Related IPs: 3
- Hashes: 329
- Industries Targeted: Education, Healthcare, Telecommunications, Banking, Finance, and Food & Beverage
- Vulnerabilities: CVE-2018-8453, CVE-2019-2725, CVE-2019-19781, and CVE-2019-11510.
- Threat Actors: Carbank and Gold Southfield.
HAFNIUM – Trending Threat Actor
HAFNIUM, a highly sophisticated threat actor group from China is notable for targeting US entities for data exfiltration from several industry sectors. HAFINUM was flagged by Microsoft in March 2021, and is known for primarily targeting Microsoft Exchange Servers. This threat actor exploits vulnerabilities in the system or uses stolen passwords in an attempt access exchange servers. Once successful, it creates web shell to remotely control the compromised devices.
This group uses US based VPS servers to conduct data exfiltration and the exfiltrated content is passed to MEGA – a popular site sharing site.
As per a research report released by Microsoft:
“HAFNIUM has previously compromised victims by exploiting vulnerabilities in internet-facing servers, and has used legitimate open-source frameworks, like Covenant, for command and control. Once they’ve gained access to a victim network, HAFNIUM typically exfiltrates data to file sharing sites like MEGA.”
HAFNIUM References From KNOW
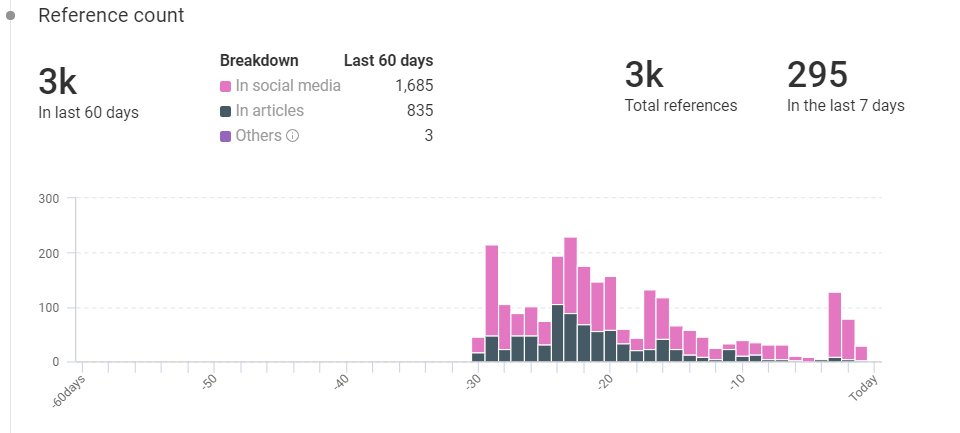
- Total references: 3,000
- Last 60 days: 3,000
- Previous 7 days: 295
Twitter Reactions for HAFNIUM
Lots of Exchange servers still vulnerable. Especially in North America and West Europe. Check out my livestream from last friday for more details: https://t.co/ex6dNHm8UL #HAFNIUM #DearCry pic.twitter.com/vPxSReYTai
— Maarten Goet (@maarten_goet) March 22, 2021
ICYMI: Find out what you need to know about the Microsoft Exchange Server attacks, including how Symantec stops them, and details on some post-compromise activity. Read now: https://t.co/SQBWWCgvTn #ProxyLogon #HAFNIUM pic.twitter.com/f8xVntIdPP
— Threat Intelligence (@threatintel) March 17, 2021
CVE-2021-22986 – Vulnerability Of The Week
CVE-2021-22986 hit the news lately when F5 Networks, a leading provider of enterprise networking gear, has announced four critical remote code execution (RCE) vulnerabilities affecting most BIG-IP and BIG-IQ software versions.
These vulnerabilities include:
- CVE-2021-22986
- CVE-2021-22987
- CVE-2021-22991
- CVE-2021-22992
The most critical one is CVE-2021-22986, and it can be exploited for unauthenticated, remote code execution attacks. F5 discovered two attack vectors that attempted to execute code on the vulnerable server.
- The first one is an attack chain that contains an SSRF attack and attempts to gain an authenticated session token as the first level, followed by remote command execution as the second level.
- The second vector is a remote command execution (RCE) that targeted the “mgmt/tm/util/bash” URL, which allows an authenticated user to execute commands using the ‘utilCmdArgs’ parameter.
Twitter Reacts To CVE-2021-22986
NEW: Threat actors have begun attacks against F5 networking devices using recent major bug (CVE-2021-22986 — unauth RCE in a management API)https://t.co/ACA9FlBe2x pic.twitter.com/qsGjQHHDw9
— Catalin Cimpanu (@campuscodi) March 19, 2021
F5 urges customers to patch 4 critical BIG-IP pre-auth RCE bugs – @sergheihttps://t.co/1CyGdEejWw
— BleepingComputer (@BleepinComputer) March 10, 2021
What is KNOW and How it Helps?
KNOW is Netenrich’s threat intel platform that scores intel from billions of data points and provides relevant and expert analyst insights, in a fraction of the time that it takes now. As a cybersecurity professional, the insights from KNOW will help you identify the latest trends, search and take decisive steps for your organization. The trending threats dashboard gives you a detailed view of the most relevant information to help you with insights on trending activities in the last 7 and 60 days.
All the context and detailed insights and reports are for free, so why not take advantage of KNOW? Get to KNOW for free cybersecurity news and threat intelligence at your finger tips.
Subscribe To Our Newsletter!
The best source of information for Security, Networks, Cloud, and ITOps best practices. Join us.
Thank you for subscribing!




