The threats typically arrive by email and include victim-specific data such as Autonomous System Numbers (ASN) or IP addresses of servers or services they will target if their demands are not fulfilled. The attacks are not continuous but executed regularly enough to disrupt the victim and cause damage to their business and reputation. Both APT28 Fancy Bear And Evil Corp are highly referenced on our KNOW’s threat intel dashboard. Let’s look at each actor in detail and analyze the data we have from KNOW.
Before we get started, check out last week’s threat actor — Hidden Cobra — and view everything that you need to KNOW.
Threat actor 1: APT28 Fancy Bear
APT 28 aka Fancy Bear aka Sofacy is a highly sophisticated threat group, which is sponsored by the Russian government and operational at least from 2004. This group is responsible for attacks against the German parliament, the White House, NATO. Currently, APT28 leverages ‘VPNFilter’ to actively infect Ukraine based IoT devices. This malware is equipped with self-destructive capabilities, and is able to monitor Modbus SCADA protocols.
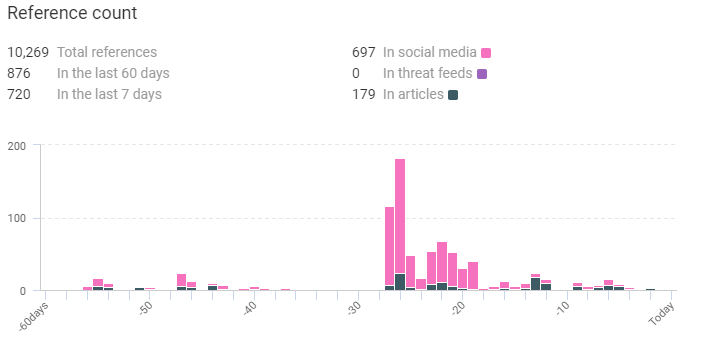
Fancy Bear has several other aliases namely Tsar Team, Group 74, Sofacy, etc.
Infamous Fancy Bear attacks
#1 The New Zealand Stock Exchange Attack
Just when you thought 2020 couldn’t get any stranger, we’ve now got armies of infected “zombie computers” attacking institutions including the New Zealand stock exchange and the national weather bureau. The actors conducting the campaign are believed to be those who have previously purported to be Russian cyber espionage group Fancy Bear and the Armada Collective.
#2 Fancy Bear penetrates Democratic National Committee server
In 2016, the notorious Russian hacker group known as Fancy Bear had penetrated a DNC server “at the heart of the network.” By that point, the intruders already had the ability to delete, alter, or steal data from the network at will. And somehow the breach had come as a terrible surprise—despite an FBI agent’s warning to Tamene of potential Russian hacking over a series of phone calls that had begun fully nine months earlier.
Context from KNOW
Industries affected by Fancy Bear
Important data captured by KNOW
- Risk rules triggered –
- Recent sandbox sighting – 3 sighting(s)
- Historically linked to malware – 385 sighting(s)
- 2 related malware: Lojax, Drovorub.
- Historically linked to intrusion method – 27 sighting(s) – phishing, obfuscation, phishing campaign, zero day, business email compromise, spam, password stealer, etc.
- Historic Sandbox Sighting – 190 sighting(s)
From the Twitterverse
If you missed it and you look for a reading, please take a look here. #APT28 Attacks Evolution https://t.co/EpJjyaR32a #cybersecurity
— Marco Ramilli (@Marco_Ramilli) July 23, 2020
Fancy Bear is moving into Linux malware https://t.co/DtHLNa8K5G
— iTech News (@NewsItech) August 14, 2020
In this Buffer Overflow Podcast, Host: Ned Bellavance & Enterprise Architect: Chris Hayner discuss Browser Extensions, clickbait, malware, uBlock, Privacy Badger, plus the NSA’s Fancy Bear + Cloud Battles! ☞ https://t.co/Ntlrq4IGC8 pic.twitter.com/3zheBHAWHR
— Anexinet (@anexinet) August 25, 2020
Threat actor 2: Evil Corp
The Evil Corp is a large cybercrime group that is originally known for its use of the Dridex banking Trojan. In recent years, it has demanded ransom payments to the tune of $500,000 to $1 million, according to security researchers. Evil Corp uses compromised credentials to transfer funds from a victim’s bank account to those of accounts controlled by the group. “As of 2016, Evil Corp had harvested banking credentials from customers at approximately 300 banks and financial institutions in over 40 countries, making the group one of the main financial threats faced by businesses,” the US Justice Department said in a statement last year.
Evil Corp specializes in targeting the United States and British financial services sector through their use of the Dridex malware and is thought to have stolen at least US $100 million to date.
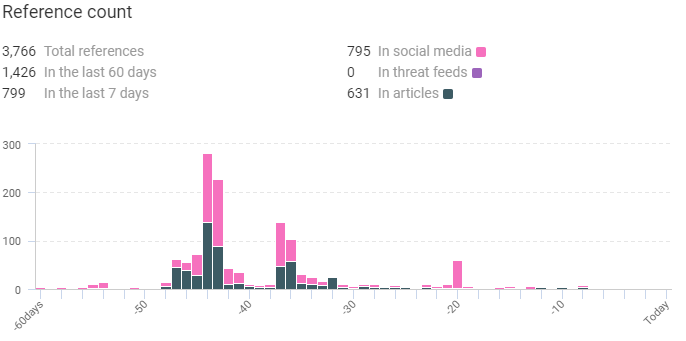
Evil Corp attack techniques
#1 Attacks are timely and targeted
Garmin was an attractive target for Evil Corp, whose ransomware is believed to be used in the attack on its data and systems. “We saw that Evil Corp targeted Garmin because they knew they were a large corporation with both deep pockets and mission-critical data, which meant they’d pay up,” said Chloé Messdaghi, vice president of strategy at Point3 Security, a provider of training and analytic tools to the security industry.
#2 WastedLocker uses Windows Cache Manager
Over the past few weeks, the WastedLocker Ransomware has become notorious after being attributed to the sanctioned Evil Corp hacking group and used to attack Garmin. To increase Windows’s performance, commonly used files or files specified by an application are read into and stored in the Windows Cache, which utilizes system memory. To bypass detection by anti-ransomware solutions, WastedLocker includes a routine that opens a file, reads it into the Windows Cache Manager, and then closes the original file.
Context from KNOW
Industries affected by Evil Corp
Important data captured by KNOW
- Risk rules triggered –
- Recent sandbox sighting – 1 sighting(s)
- Historically linked to malware – 996386 sighting(s)
- 8 related malware – Dridex, Gozi, Gozi ISFB, BitPaymer, FriedEX, Cobalt Strike, WastedLocker, etc.
- Historically linked to intrusion method – 13 sighting(s) – obfuscation, phishing, data exfiltration, data breach, social engineering, exfiltrate data, credential dumping, etc.
- Historically linked to C&C server – 1 sighting(s)
From the Twitterverse
US Companies Hit With A New Ransomware Campaign: The hacking group known as Evil Corp. has attacked major US companies using a dangerous new strain of ransomware called #WastedLocker. https://t.co/fQqyxoVYRX @symantec pic.twitter.com/e0C7s6s9aM
— CyberSecInt (@CyberSecInt) July 29, 2020
Read how #ransomware groups have evolved to operate as professional businesses w/guaranteed turnaround times and real-time chat support. They pinky-swear not to attack hospitals, schools, nonprofits, or government targets. #DarkSide #Maze #EvilCorp #REvilhttps://t.co/jxiMczK0sc
— Jorge Orchilles (@jorgeorchilles) September 1, 2020
Russian malware hackers charged in evil corp $100 million bank scheme | #Databreach | Pentest | #Hacker https://t.co/unf1aitwKb
— National Cyber Security (@NcsVentures) August 23, 2020
What is KNOW?
KNOW is Netenrich’s Threat Intel Platform that extracts data from billions of data points and correlates relevant intel and expert analyst insights to help you follow, search, and act—in a fraction of the time it takes now.
One of KNOW’s handiest tools is the trending threats dashboard, which gives you a bird’s eye view of the most potent malware, threat actors, methods, and vulnerabilities in the following time frames:
- Last 7 days.
- Last 60 days.
So, want to check out KNOW some more? Why don’t you sign up? Did we mention that it’s completely free?
Or subscribe to get daily threat intel updates.
Subscribe To Our Newsletter!
The best source of information for Security, Networks, Cloud, and ITOps best practices. Join us.
Thank you for subscribing!




