Start Your Security Journey
With Google SecOps Implementation from Netenrich
Lay the foundation for long-term success
Customers have different needs at different times during their security journey. If you’re just beginning yours and are new to Google SecOps, our implementation service is an excellent option to get you headed down the right path.
Our Google SecOps Implementation service helps customers get smoothly onboarded and ready to reap the manifold benefits of Google SecOps as quickly as possible. As part of the onboarding and guided deployment process, our team of security engineers works closely with you to properly set up critical elements, such as data ingestion, detection, and written indicators of compromise.
Google SecOps Implementation delivery
- Seamless integration of Google SecOps with your existing infrastructure.
- Identification and ingestion of critical data sources with integration of premium intelligence.
- Deployment and fine-tuning of detection rules and UEBA for enhanced threat identification.
- Enablement of swift incident response through seamless SOAR integration.
- Delivery of key insights with customizable dashboards and reports.

Why choose Google SecOps Implementation from Netenrich?
Seamless integration of Google SecOps into your operational workflow doesn't have to be difficult, costly, or time-consuming.
As certified Google SecOps experts, we excel at delivering a comprehensive and cost-effective Google SecOps implementation service, which includes training programs and dedicated support staff to ensure a successful start to your security journey.
Ongoing tier-1 product support for Google SecOps available
Unwavering support from Netenrich team of security engineers to help you maintain peak performance of your Google SecOps solution.
Ongoing CSM, project, and/or program management of Google SecOps available
Dedicated Customer Success Manager (CSM) to ensure continued success and benefits.
Managed Google SecOps available
Choose Managed Google SecOps to offload administration, maintenance, tuning, and management of Google SecOps to Netenrich, so that your security team can focus on strategic work.
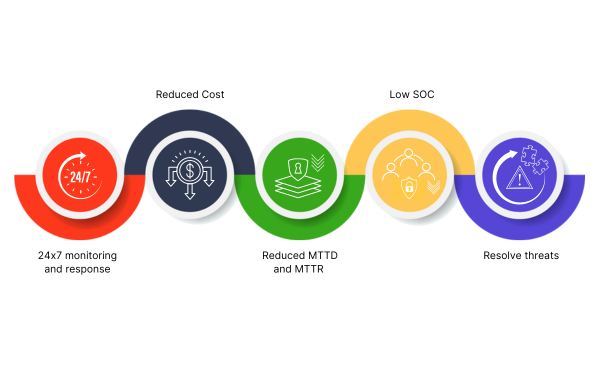
Work from a common operational view
Siloed security and digital ops leads to gaps and inefficient duplication of tools, processes, and people. Resolution Intelligence Cloud provides a common operational view and situational awareness aligned to business risk. And it facilitates collaboration within and between teams.
- Strengthen your security posture
- Improve performance and up time
- Boost analyst effectiveness
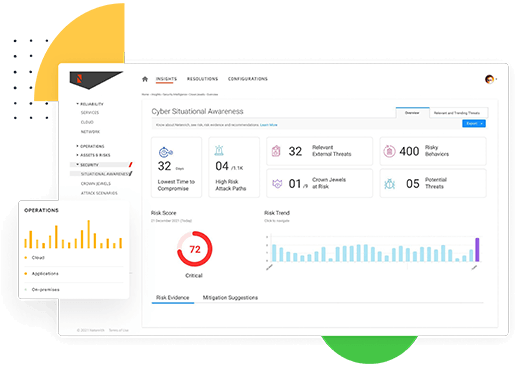
Out-innovate hackers with anomaly detection & situational awareness
Hackers are relentlessly innovative. It's futile to fight them with traditional, reactive methods.
- Identify unknowns without detection rules with advanced anomaly detection (think next-next-gen UEBA)
- Be proactive with actionable insights from data over time, correlated and mapped to the MITRE ATT&CK framework
- Identify and resolve what matters most to the business — stop wasting time on alert noise
- Communicate across functions and coordinate response fast
Trusted by











%201.png?width=400&height=176&name=MicrosoftTeams-image%20(1)%201.png)

